FAQ
Can't I just cheat by looking at the flags in GitHub?
Yep
Can't I just cheat by getting all the flags with my admin user?
Yep
Can I publish walkthroughs on the live CloudFoxable challenges?
Yep
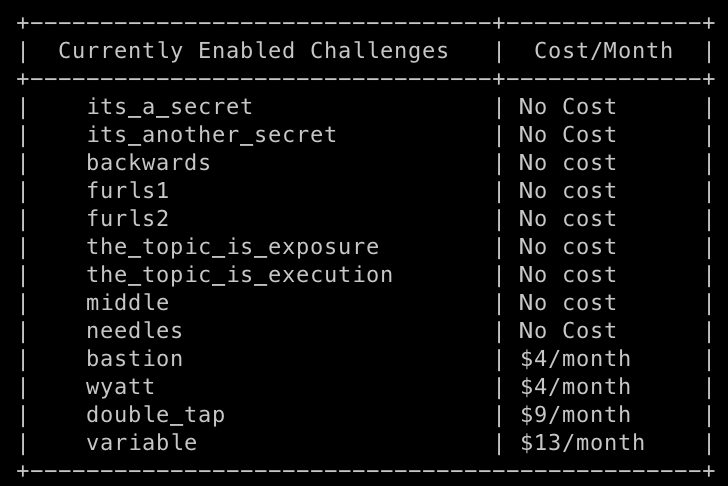
How much will this cost me?
Many challenges have no cost associated with them. They are enabled by default.
Challenges that do have a cost associated with them are disabled by default and need to be manually enabled.
Every time you enable a new challenge you will get a summary the currently enabled challenges and how much they cost per month, like this:
Should I deploy CloudFoxable into an existing environment that I use for production stuff?
No! Please deploy CloudFoxable into a new or existing playground/sandbox/learning account.
Even though it's in a playground account, is there any way someone else can compromise my CloudFoxable resources?
There shouldn't be. The following safeguards are in place, but please reach out if you think we missed something:
- Source IP restrictions - Like CloudGoat, the terraform code finds your current IP address and uses that as a whitelist for anything that is exploitable from the public. There are a few exceptions: There are some resources that are truly public to everyone, but they either have randomized hostnames, or just don't lead to any attackable surface area. For instance, there's an SQS queue and an SNS topic that anyone can send messages to, but nothing else interacts with these resources.
- No paths lead to admin - None of the CloudFoxable challenges lead to admin, so even if someone did find something exploitable, they should only be able to get to the FLAG.
Please submit an issuue if you notice any publicly accessible exploit paths that put user's CloudFoxable environments at risk (other than access to the flags).
I've never used Terraform and I'm afraid of it. Help!?
I was also afraid of Terraform and projects that would create resources in my account before I knew how Terraform worked. Here are some things that might ease your anxiety:
- By using an AWS account for this single purpose, you can rest assured that this repository won't negatively impact anything else you care about. Even if you deploy CloudFoxable to a separate account in an AWS organization, you can rest assured that the other accounts in the org will be outside the blast radius of this playground account.
- The terraform plan command is a dry run. It shows you exactly what will be deployed if you run terraform apply before you actually run it.
- Rest assured knowing that you can
terraform destroyanything youterraform applyfor a clean slate. - If your concern is cost, each challenge gives you a rough monthly cost estimate.
Can I run this tool and another tool like CloudGoat, Terragoat, or SadCloud in the same AWS account?
Yes. Each tool will keep its Terraform state separately, but all resources will be created, updated, and deleted in the same account. They can coexist.